When you manage an aged care facility in Australia, protecting resident information is a major responsibility. This includes sensitive personal and health records. Strong aged care data security is not just good practice; it is a legal and ethical requirement. Without proper protections, your facility risks data breaches, which can harm your residents and your reputation. This guide will help you understand the steps you need to take to keep data safe.
Key Takeaways
- Aged care data security is critical for protecting resident privacy and meeting legal duties.
- Australian privacy principles set clear rules for handling personal information.
- Implementing strong cyber security controls helps prevent data breaches.
- Having a disaster recovery plan is important for responding to security incidents.
- Governa AI offers tools to help Australian aged care facilities meet these security needs.
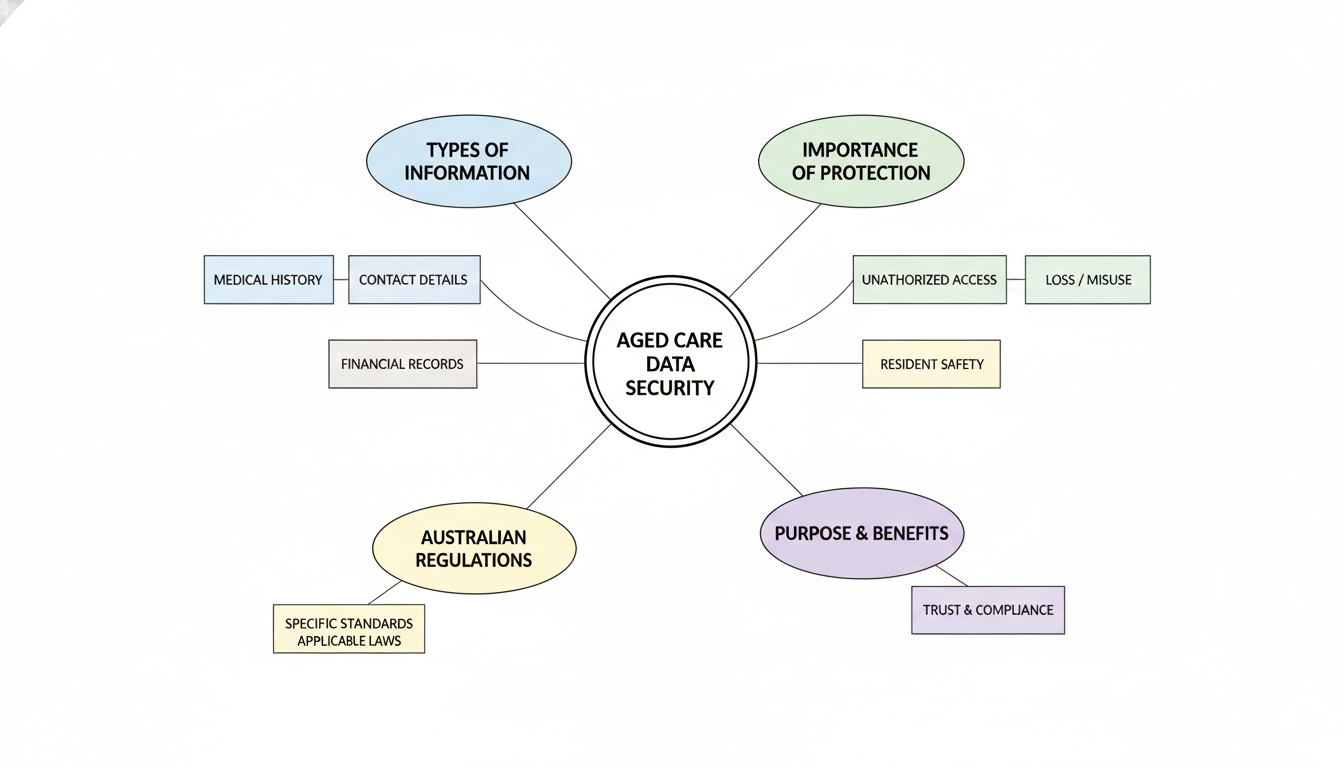
Understanding Aged Care Data Security in Australia
Aged care facilities handle a lot of personal and health information. This data includes medical history, contact details, financial records, and more. Protecting this information from unauthorized access, loss, or misuse is what aged care data security is all about. In Australia, specific standards and laws apply to how you manage this data. These rules are in place to keep residents safe and to make sure their privacy is respected.
Why Patient Data Privacy Matters
Patient data privacy is a cornerstone of trust in aged care. Residents and their families expect that their personal details will be kept confidential. When data is not private, it can lead to:
- Identity theft: Personal information can be used for fraud.
- Financial harm: Banking details could be stolen.
- Emotional distress: Residents may feel violated or unsafe.
- Loss of trust: Families might lose faith in your facility's ability to care for their loved ones.
It is important to remember that respecting privacy is a key part of providing quality care.
Essential Cyber Security Controls
To protect resident data, you need to put strong cyber security controls in place. These controls are like safeguards that stop cyber threats. Here are some important controls:
- Access Management:
- Limit who can see sensitive data.
- Make sure staff only have access to the information they need for their job.
- Use strong passwords and change them regularly.
- Use multi-factor authentication (MFA) where possible, which adds an extra layer of security.
- Data Encryption:
- Scramble data so only authorized people can read it.
- This protects data when it is stored and when it is sent over networks.
- Regular Backups:
- Make copies of all important data.
- Store backups in a secure, separate location.
- This helps you get back on track quickly if data is lost or corrupted.
- Staff Training:
- Teach all staff about cyber security risks and how to follow security policies.
- Remind them about common threats like phishing emails.
- Software Updates:
- Keep all operating systems and software up to date.
- Updates often fix security weaknesses.
- Network Security:
- Use firewalls and anti-virus software.
- Monitor your network for unusual activity.
Responding to Data Breaches: Disaster Recovery
Even with the best cyber security controls, data breaches can happen. A disaster recovery plan is your guide for what to do if a security incident occurs. This plan helps you:
- Identify the breach: Find out what happened and what data was affected.
- Contain the breach: Stop the breach from spreading further.
- Eradicate the threat: Remove the cause of the breach.
- Recover data: Restore lost data from backups.
- Notify affected parties: Inform residents, their families, and regulators as required by law.
- Review and improve: Learn from the incident to make your security stronger.
Having a clear plan helps minimize harm and ensures you meet your legal duties.
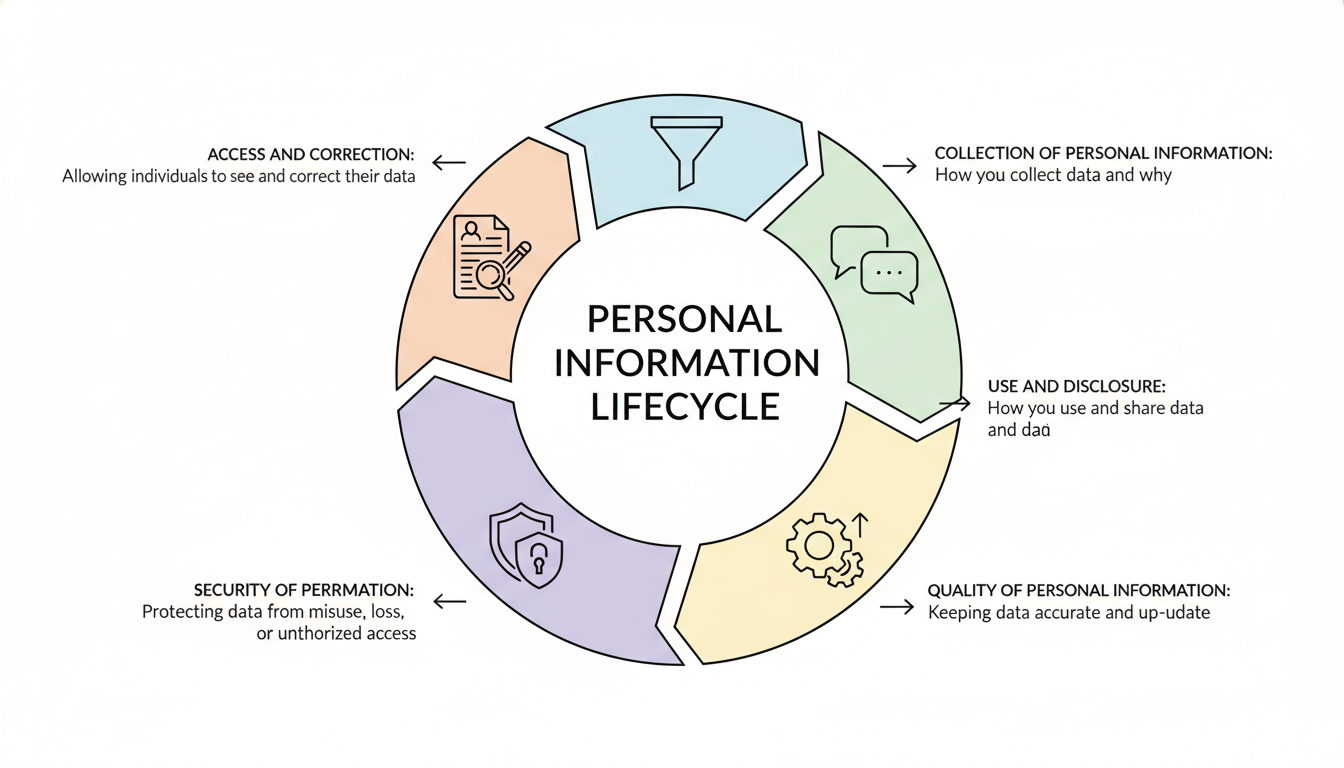
Adhering to Australian Privacy Principles
In Australia, the Australian Privacy Principles (APPs) are a set of 13 rules that guide how organizations handle personal information. These principles cover:
- Collection of personal information: How you collect data and why.
- Use and disclosure: How you use and share data.
- Quality of personal information: Keeping data accurate and up-to-date.
- Security of personal information: Protecting data from misuse, loss, or unauthorized access.
- Access and correction: Allowing individuals to see and correct their data.
Understanding and following the APPs is essential for all aged care providers. You can find more information on the Digital Health website about standards for aged care clinical information systems. For example, the Aged Care Clinical Information System (ACCIS) standards help guide how you manage digital health records: https://www.digitalhealth.gov.au/standards/aged-care-clinical-information-system-accis-standards.
Governa AI's Role in Data Protection
Governa AI understands the unique data security challenges faced by Australian aged care facilities. We provide tools and solutions designed to help you strengthen your aged care data security. Our services focus on:
- Compliance: Helping you meet Australian privacy principles and other regulations.
- Risk Management: Identifying and reducing potential security weaknesses.
- Data Protection: Implementing robust cyber security controls to safeguard resident information.
By partnering with Governa AI, you can be more confident that your facility's data is well-protected, allowing you to focus on providing excellent care.
Frequently Asked Questions
What is aged care data security?
Aged care data security involves protecting the personal and health information of residents in aged care facilities from unauthorized access, loss, or misuse. This includes using technical and organizational measures to keep data safe.
Why is patient data privacy important in aged care?
Patient data privacy is important because it builds trust with residents and their families. It also prevents potential harms like identity theft, financial fraud, and emotional distress that can result from a data breach. It is also a legal requirement under Australian law.
What are some basic cyber security controls I should use?
Basic cyber security controls include managing who can access data, encrypting sensitive information, regularly backing up data, training staff on security, keeping software updated, and using network security tools like firewalls.
What should I do if a data breach occurs?
If a data breach occurs, you should follow your disaster recovery plan. This typically involves identifying the breach, containing it, removing the cause, recovering any lost data, notifying affected individuals and regulators, and reviewing the incident to improve future security.
Where can I find information about Australian privacy principles?
You can find detailed information about the Australian Privacy Principles (APPs) on the website of the Office of the Australian Information Commissioner (OAIC). The Digital Health website also provides relevant standards, such as those for Aged Care Clinical Information Systems.


.png)
.png)